Sammy Kamkar, security researcher, whistleblower and expert in “applied hacking”, recently revealed his latest masterstroke, which should worry Web users and IT security managers alike. PoisonTap, a device running on an inexpensive Raspberry Pi nano-computer, can easily take control of any computer connected to the Internet. PoisonTap works on both Windows PCs (and probably Linux) and Macs, even when locked. Here’s how.
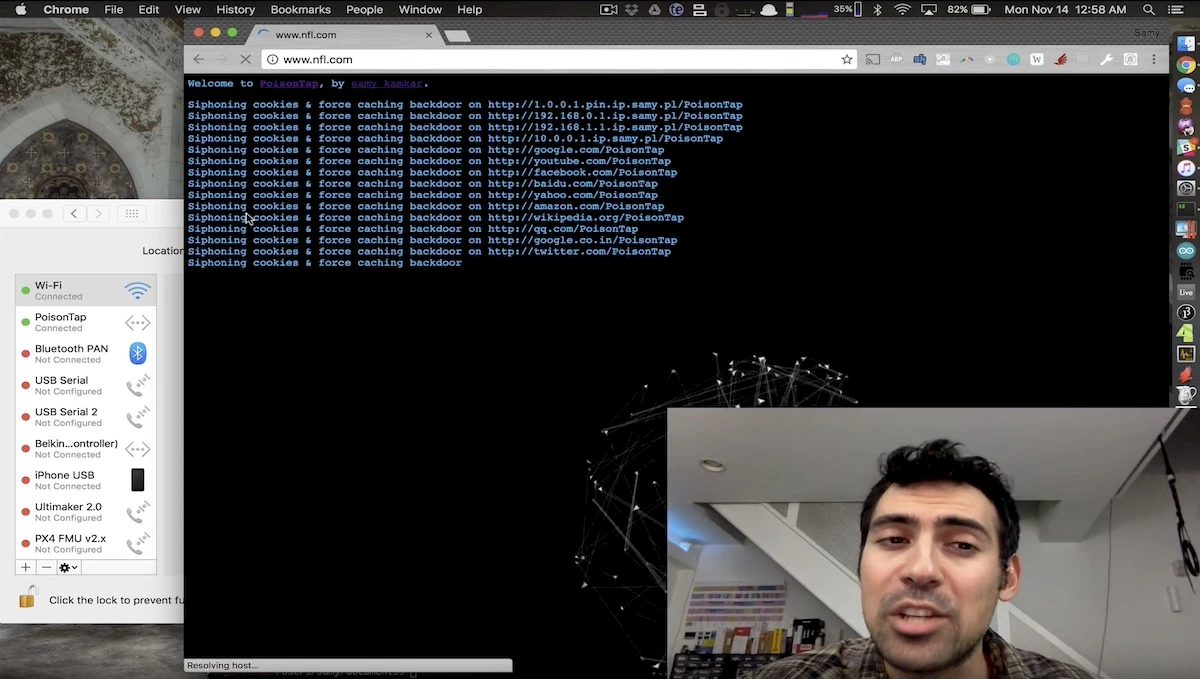
PoisonTap requires no advanced skills to operate. It boots up when connected to a USB port, posing as an Ethernet-over-USB device. The computer recognizes it as such and sends it a DHCP request, to which PoisonTap returns an IP address. But PoisonTap’s (black) “magic” is to send its DHCP response in such a way as to make the computer believe that all IP addresses on the Internet are part of PoisonTap’s pseudo-local network. The result is that the computer sends all Internet traffic to PoisonTap rather than to its main interface. PoisonTap then searches for an open Web browser – even an inactive one in the background will do – from which it launches its attack, siphoning cookies while installing back doors for thousands of popular sites. Hacked computers are then forced to make requests using its user’s cookies, allowing the hacker to pose as the user remotely. All in less than 30 seconds.
PoisonTap’s Key Features
- Does not require the computer to be unlocked.
- Emulates an Ethernet peripheral on USB (or Thunderbolt).
- Diverts all Internet traffic from the main interface, acting as if its local Ethernet network contained the entire IPv4 space (0.0.0.0 - 255.255.255.255). The trick is that LAN traffic has priority over Internet traffic.
- From the Web browser, siphons and stores all HTTP cookies (session and persistent) for the top 1,000,000 Alexa Web sites.
- Installs a permanent back door in the browser’s cache (HTML+JavaScript) for each Alexa-listed Web site..
- Exposes connected routers, making them accessible remotely through WebSocket and DNS Rebinding.
- Back doors and remote access remain enabled even after the USB device is removed.
- Allows the hacker to remotely force the machine to make HTTP requests and responses (GET & POST) using the user’s cookies for the top one million domains with a back door.
A “plausible” threat
Security expert Rik Ferguson, of Trend Micro, told the BBC the device was a plausible threat. "[In normal circumstances] Even when you are not using a web browser it is still making requests and communicating - due to updates or ads. Once the device is plugged in it exploits that communication and steals session cookies from the top one million websites," said Mr Ferguson.
An initial HTTP request is necessary to initiate the process for PoisonTap. Such HTTP requests are usually made by pages left open, even when the browser is in the background. Indeed, it would be unusual for this not to work, since at any given time, at least one page is going to be refreshing data, reloading an ad, or sending data to an analytics platform or any other usage-tracking tool for marketing purposes…
Sammy Kamkar explains how his tool works in this video:
Why would anyone even create such malware?
Kamkar’s “creations” seek to expose system vulnerabilities for all to see. “The primary motivation is to demonstrate that even on a password-protected computer running off of a WPA2 Wi-Fi, your system and network can still be attacked quickly and easily. Existing non-HTTPS website credentials can be stolen, and, in fact, cookies from HTTPS sites that did not properly set the ‘secure flag’ on the cookie can also be siphoned,” said Sammy.
Sammy’s mission seems to have been accomplished with PoisonTap…
How to protect yourself
For computers that make an easy target, you may have to physically plug up your USB ports (and Thunderbolt). Kamkar only half jokingly suggests using cement. Another suggestion is to close all of your Web browsers before leaving your machine unattended for any amount of time, which is not terribly practical for many users.

[Above: the latest addition to the IT security manager’s tool box.]
Just remember that to launch an attack, PoisonTap needs physical access first, requiring the plugging of hardware into a USB port to control the user’s Web traffic. Hence the importance of considering the enhanced vulnerability of laptop users who work on the road and in public places. Such users need to be aware of the risk; one moment’s inattention is all it takes

