T2 security vulnerability
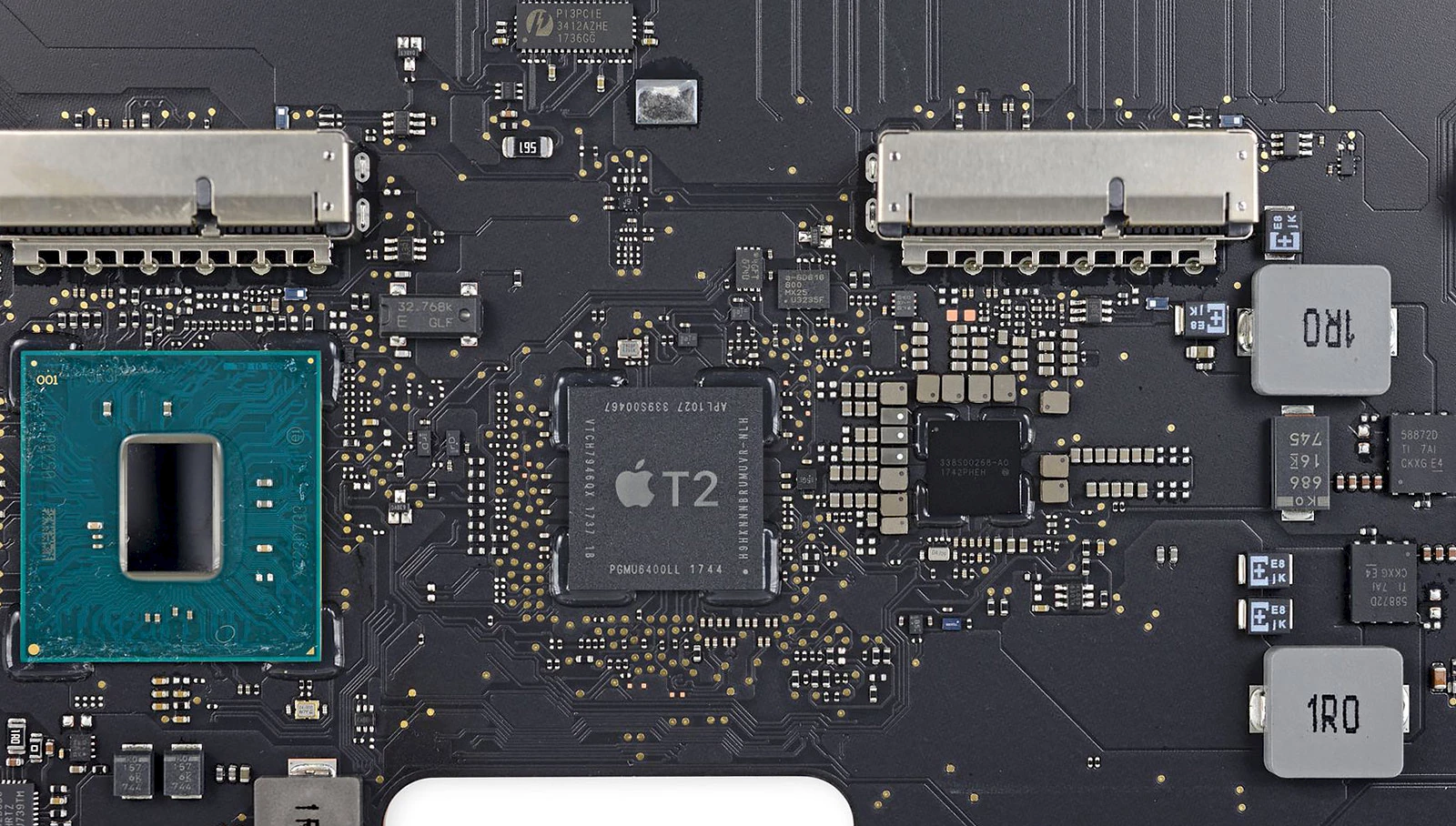
Apple’s T2 security chip. © iFixit.
A recently released jailbreak tool is letting anyone exploit a vulnerability on the more recent Macs to bypass Apple’s trusted T2 security chip and gain deep system access. While Apple may be able to slow down potential hackers, the flaw is ultimately unfixable in every Mac that has a T2 inside, since it is embedded in the T2 silicon. The T2, launched in 2017, acts as a trusted mechanism for securing high-value features like encrypted data storage, Touch ID, and Activation Lock. The vulnerability, known as Checkm8, was already present in Apple’s A5 through A11 SoC, and is still being used to jailbreak older models of iPhones with these chips. On the T2 Mac chip, it can be used to run Linux on the T2 and could also be weaponized by malicious hackers to disable macOS security features like System Integrity Protection and Secure Boot. Worse yet, combined with another T2 vulnerability that was publicly disclosed in July, the jailbreak could also potentially be used to obtain FileVault encryption keys and to decrypt user data. But don’t panic yet: an attacker would need physical access to target your device in order to exploit it, as the tool can only run off of another device over USB.
⇨ Ars Technica, Lily Hay Newman, “Apple’s T2 security chip has an unfixable flaw.”
